Wi-Fi can be KRACK-ed. Here's what to do next
- Written by David Glance, Director of UWA Centre for Software Practice, University of Western Australia
A security researcher has revealed serious flaws in the way that most contemporary Wi-Fi networks are secured.
Discovered by Mathy Vanhoef from the University of Leuven, the vulnerability affects the protocol “Wi-Fi Protected Access 2”. Otherwise known as WPA2, this encrypts the connection between a computer or mobile phone and a Wi-Fi access point to keep your browsing safe.
Read More: Equifax breach is a reminder of society’s larger cybersecurity problems
Because this security can be cracked, it’s possible for someone to read what is transmitted on the network, allowing them to intercept passwords or credit card details, or to inject malicious code when users visit websites.
Dubbed the “key reinstallation attack” (KRACK), Vanhoef’s discovery has the most serious implications for devices running the Android operating system, especially version 6.0 and above, and devices that use Linux.
But don’t freak out just yet: although almost every device that uses Wi-Fi is vulnerable, KRACK can only be deployed in certain circumstances. And there are some simple steps you can take to help keep your internet traffic safe.
What is WPA2, anyway?
Most secured wireless networks use the WPA2 security protocol. It allows users to login to a network and keep their communications secured.
The encryption process uses a set of secret keys that are agreed to between the connecting device and the wireless access point. These keys are used to scramble messages on the network and provide protection against someone sitting in an internet cafe, for example, and listening in on messages between laptops and the wireless router.
WPA2 was created to address weaknesses in previous protocols used to secure wireless networks, such as the Wired Equivalency Privacy (WEP) and the first version of WPA. Until now, it was arguably more secure.
How does KRACK work?
The KRACK attack requires the attacker to be physically close enough to a Wi-Fi network to perform a “man-in-the-middle” attack.
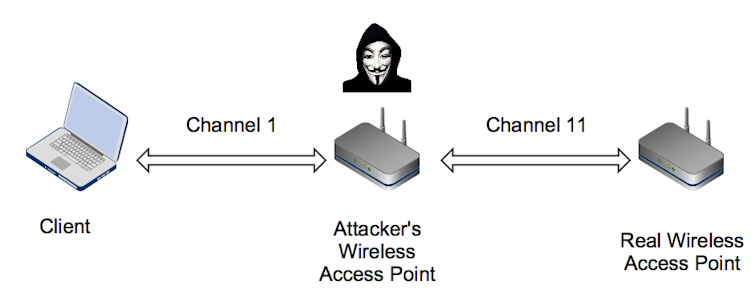 Man-in-the-middle channel attack.
David Glance
Man-in-the-middle channel attack.
David Glance
Most Wi-Fi networks use a “4-way handshake”. This is a series of messages between the client and the access point used to ensure both parties have the right credentials.
In this scenario, the attacker can prompt the third message to be resent, which causes an existing key to be reused. These keys are used to scramble the contents of messages to prevent them from being read, but also to check if messages have been altered in any way. By forcing the reuse of old keys, these protections are effectively removed.
Because the key that is reused is set to zeros in Android 6.0 devices, messages can be more easily decrypted. On other platforms, and depending on the circumstances, only some messages can be exposed.
The KRACK in action.What does this mean for you?
Vendors of affected devices have apparently known about the vulnerability since July or August. Since the attack is against Wi-Fi clients, devices like mobile phones and laptops are most at risk.
Make sure you update your devices
Apple and Google have told media outlets that they will have fixes for the flaw ready in a few weeks. Microsoft has already released a fix, and other companies will have either already fixed the vulnerability or have fixes shortly.
The key message is that you should immediately apply all updates that come out for phones, laptops or other devices. This is especially true for Android phones.
Use sites with HTTPS
Until patches are available, it is worth remembering that Wi-Fi networks, even when secure, only protect communications up until the wireless access point. For end-to-end protection with websites, we rely on HTTPS to keep communication secure. Make sure you look for it in the URL of sites you visit.
Normally this would protect users even on a compromised network, although it is possible to bypass HTTPS if the website is not securely configured.
Read More: Using truly secure passwords: 6 essential reads
Use encrypted services
Other communications, such as those used in sending and receiving email, should also be encrypted. Although this is not always the case.
Services like Gmail are encrypted by default. Other applications that use their own end-to-end encryption like Facebook Messenger, WhatsApp and FaceTime would also be secure.
Get a VPN
One way of ensuring secure communication while using any form of Wi-Fi network is to use a Virtual Private Network (VPN) connection.
VPNs provide their own encryption, which protects all communication sent over the Wi-Fi network and would still provide that safeguard, even in the case of someone using the WPA2 KRACK.
We’re not all doomed
Although this is a serious breach, it is not a simple one technically and requires the attacker to have proximity to the Wi-Fi network. The attacker also has to rely on the attacked device going to unprotected, non-HTTPS sites and to not be using a VPN.
As industry commentators have pointed out, this is not quite as serious as media headlines might suggest. But consider it a timely reminder to install software updates on all your devices.
Authors: David Glance, Director of UWA Centre for Software Practice, University of Western Australia
Read more http://theconversation.com/wi-fi-can-be-krack-ed-heres-what-to-do-next-85746





